USB 3.0 NAND Flash Controller IC Family
Overview
• VLS 3100 Secure USB 3.0 Pen Drive Controller (Single Channel, QFN-48)
• VLS 3200 Secure USB 3.0 Pen Drive Controller (Dual Channel, QFN-64)
• VLS 5100 General Purpose USB 3.0 NAND Flash Controller (Single Channel, QFN-64)
• VLS 5200 General Purpose USB 3.0 NAND Flash Controller (Dual Channel, QFN-88)
High Performance . Low Power
- Throughput up to 120MBps (Single Channel), 200MBps (Dual Channel)
- Hardware Accelerator / DMAC / NFC
- Programmable Clock Speeds with Power Gating Support
Security
- Proprietary Patent Pending UCA Technology
- Hardware-based AES Encryption Engine
Flash Memory Support . Reliability . Low Cost
- SLC, MLC, TLC NAND Flash Devices from Intel, Micron, Samsung, Hynix, …
- 2KB, 4KB, 8KB Page Sizes supporting Multi-LUN and Multi-Plane features
- ONFI 2, Toggle, Toggle 2, Async NAND Flash Memory Interfaces
- Programmable 26-bit, 29-bit, 30-bit, 60-bit ECC options
- Built-in 3.3V, 1.8V, 1.0V Power Supplies from 5V
Target Applications . Time to Market
- VLS 3100, VLS 3200 : Pen Drive Applications
- VLS 5100, VLS 5200 : Multiple Applications with I2C, SPI, UART, GPIO Interfaces
- Both Reference Designs and Custom Solutions are available
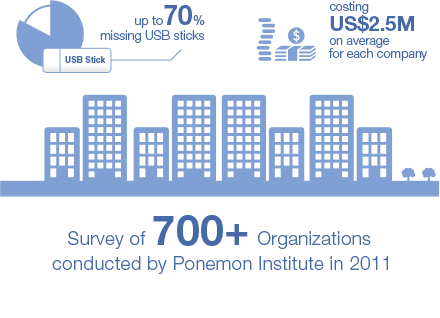
Based on a recent survey of 700+ companies, missing USB sticks represents 70% of all data breaches, costing US$2.5M on average for each company.Velosti Technology offers the most comprehensive security solution, authenticating both users and computers simultaneously.
Our hardware AES-based encryption engine provides superior security while experiencing true USB 3.0 throughput.
Unlike traditional password-only security solutions, our proprietary UCA (User-Computer-Authentication) security algorithm does not depend strictly on your password strength. Instead, UCA technology supports concurrent user and computer authentication. In other words, authorized users can only access their sensitive data in registered computers.
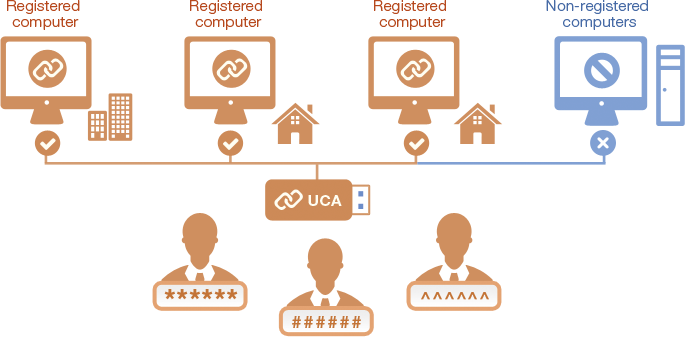
All storage data are encrypted using an AES cipher key, which can only be calculated using authorized user passwords and registered computer signatures. Our proprietary patent pending UCA technology can support multiple users and multiple registered computers, suitable for both personal and enterprise applications.